DLL planting in Bitdefender Antivirus Free 2020
TL;DR
An elevation of privilege vulnerability (CVE-2020-8094) exists in Bitdefender Antivirus Free 2020 due to DLL planting in a default folder, resulting in low privileged users being able to execute code as SYSTEM via a specially crafted DLL file.
Description
DLL planting vulnerability in testinitsigs.exe versions 3.0.16.110 and lower, as used in Bitdefender Antivirus Free 2020 versions prior to 1.0.16.148 allows an attacker to load an arbitrary DLL file from the search path.
The testinitsigs.exe file attempts to load the httpproxy.dll module via LoadLibraryW from directories in the PATH environment variable. These include the %LOCALAPPDATA%\Microsoft\WindowsApps folder which is writable on latest Windows 10 systems by default. The testinitsigs.exe <sigType> <sigPath> command is automatically executed after signature updates in the context of the local SYSTEM account. This vulnerability allows low privileged users to execute code as SYSTEM via a specially crafted httpproxy.dll file. Note that Bitdefender Total Security loads its own httpproxy.dll module via LoadLibraryExW hence the paid version of the application is not affected by this issue.
Exploitation
- Drop malicious
httpproxy.dllin the%LOCALAPPDATA%\Microsoft\WindowsAppsdirectory. - Install Bitdefender Antivirus Free.
- Application automatically executes
testinitsigs.exeafter installation. - The
httpproxy.dllmodule is loaded bytestinitsigs.exeand the malicious code is executed.
PoC
For the purpose of this test, I have created a DLL module that invokes cmd.exe to execute the whoami command and write the output to a text file. The below screenshot shows the events related to testinitsigs.exe captured by Process Monitor. We can see that the process loads the malicious httpproxy.dll module and writes the output of the whoami command to the httpproxy.txt file in the C:\Users\Public directory.
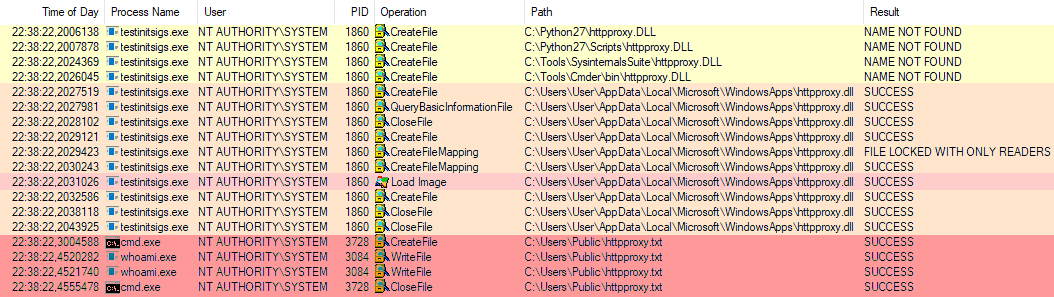
Exploitation flow in Process Monitor
Timeline
⬅️ 2020-01-19: Reported issue to Bitdefender.
➡️ 2020-01-28: Bitdefender confirmed the vulnerability.
⬅️ 2020-01-28: Requested target date and CVE identifier.
➡️ 2020-01-30: Bitdefender indicated that the fix is ready for CVE-2020-8094.
➡️ 2020-02-07: Coordinated public release of advisory.
